Top 13 Cybersecurity Trends to Follow in 2025
Learn about 13 cyber security trends for 2025 and don't give cybercriminals a chance.
The number one cybersecurity threat today will be software vulnerabilities combined with the lack of understanding of how online attacks usually work. We collected the top cybersecurity trends emerging in 2025 in industries ranging from healthcare and higher education to retail and banking.
According to a cybersecurity trends report by McKinsey, dangers doubled between 2021 and 2022, which means that the year 2025 is likely to reveal more security issues.

In the article, we will look into the future of cybersecurity discovering some of the most interesting future cybersecurity trends connected to different business areas and technology fields.
Remote Working Cybersecurity
Cybersecurity risks are often associated with the actions of tech-savvy hackers and other cybercriminals. However, unsecured networks and indiscreet users are also very likely to open the doors to data breaches and unauthorized access. This is why optimization of digital security is one of the most important network security solutions and trends in software development now.
The sophistication and the number of digital attacks have increased dramatically since the Covid-19 pandemic when millions of people worked remotely, often leaving their devices not properly protected.
These are the main online threats your employees may encounter in home offices:
- Not having access management systems, secure firewalls, password managers, and other software that your company’s office is equipped with.
- Not scan their laptops and smartphones to ensure they have the latest versions of antivirus software.
- Not checking their devices for spyware and malware.
- Not being cautious with emails – according to recent statistics, 97% of Internet users find it hard to identify phishing links.
- Leaving their devices unattended or losing them, leads to exposure of sensitive information.
The work-from-home digital security has become one of the most important trends of cybersecurity, especially in larger companies. The sophistication and the number of digital attacks have increased dramatically since the Covid-19 pandemic when millions of people worked remotely, often leaving their devices not properly protected.
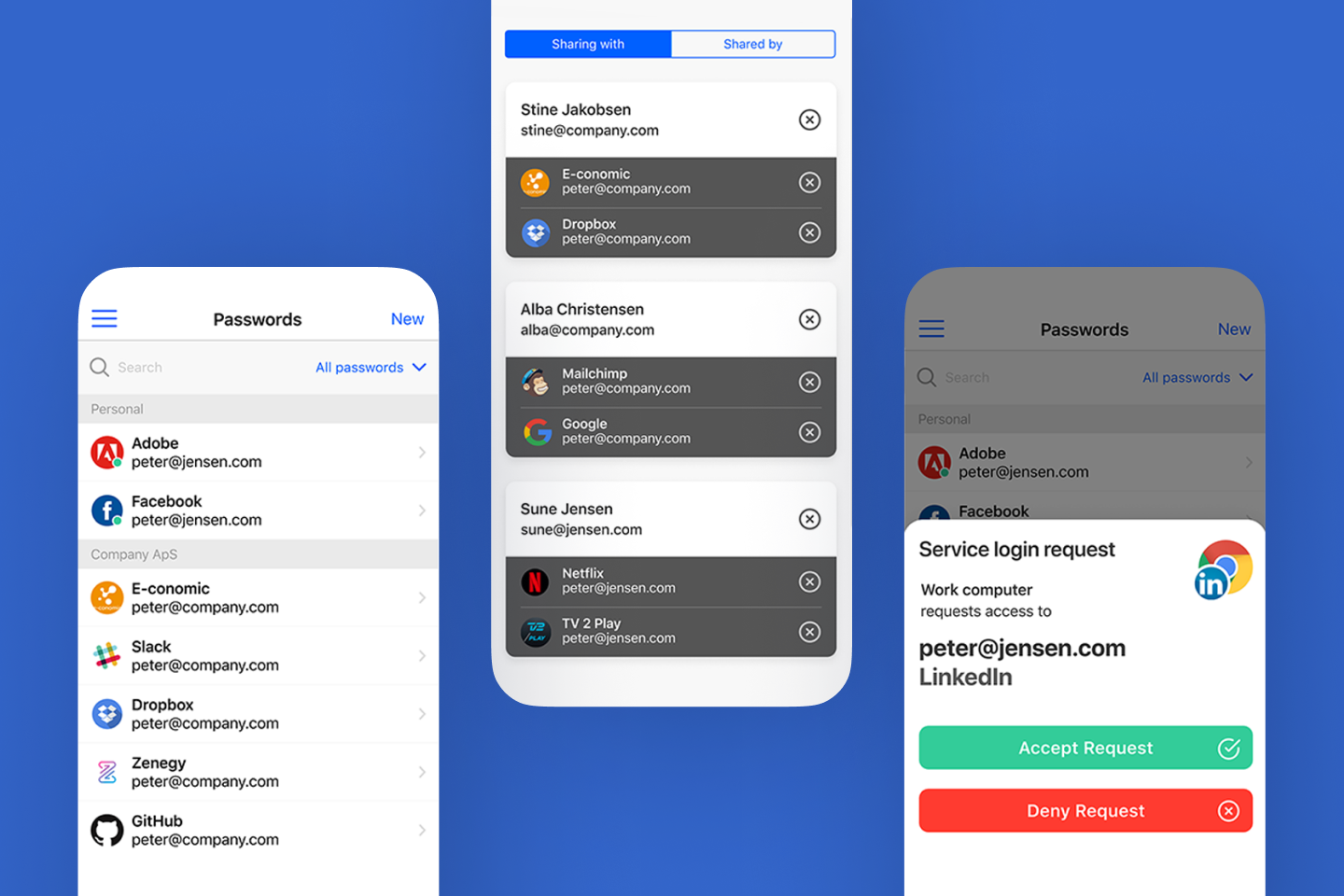
Nowadays, the widely spreading work-from-home culture and actively developing IoT technology create more security issues and new sophisticated solutions for security teams.
These strategies enable companies to mitigate security risks associated with remote and hybrid working:
- Providing sufficient monitoring and documentation;
- Identifying vulnerabilities;
- Implementing strong IT protocols;
- Enabling multi-factor authentication;
- Teaching employees how to share confidential data and how to avoid common threats like phishing attacks.
Raising user awareness is an effective means of data protection and a highly important example of cybersecurity trends for 2025 and the upcoming years.
Cybersecurity Trends in Healthcare: More Attacks on This Sector
Many healthcare providers have become a target of cyber attacks in recent years. Therefore, creating new ways to assess security risks in real time will become one of the main trends of cybersecurity in the healthcare industry in 2025.
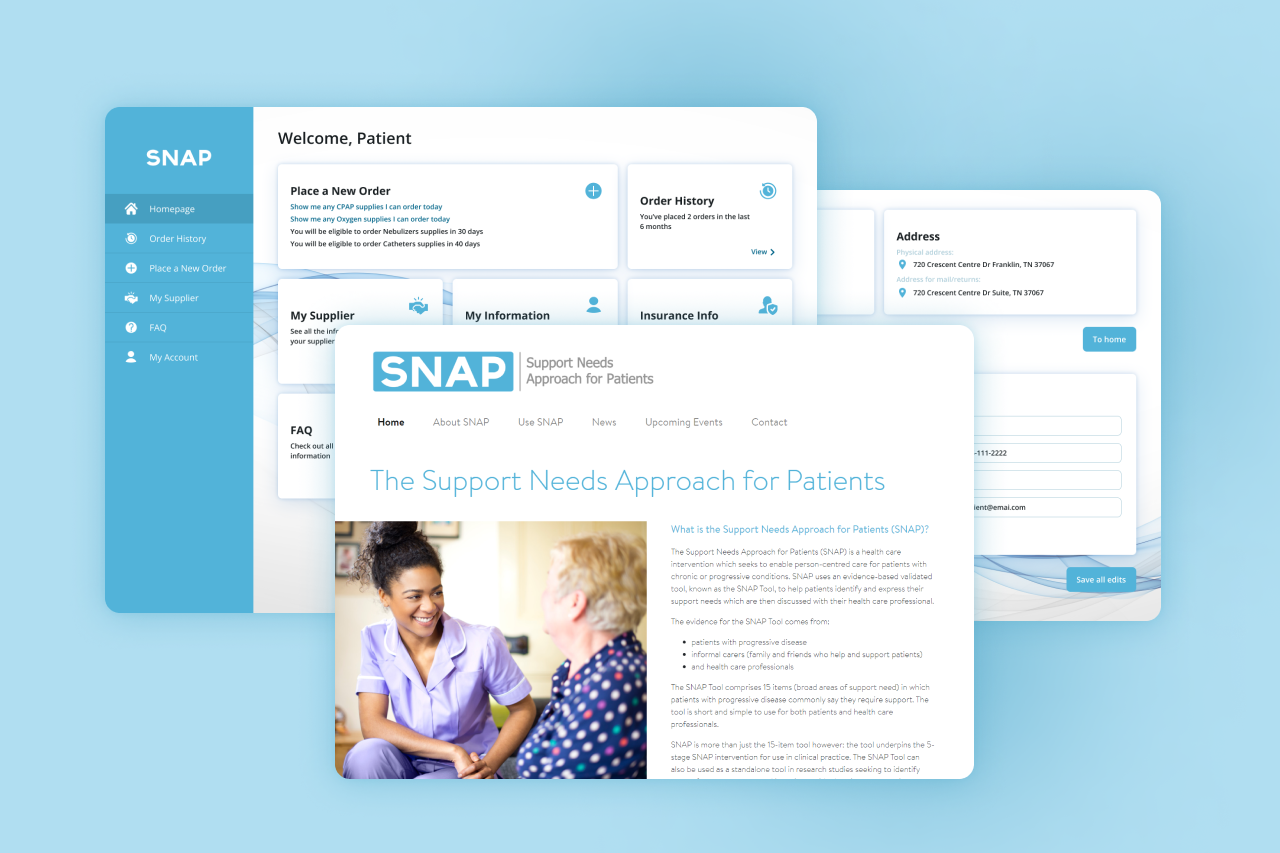
Patients’ records and other sensitive data being stolen or exposed is a huge problem that requires secure technology solutions combined with employee training on digital security. The nearest future of cybersecurity in this sector is growing budgets – estimated at 9.78 billion in 2019, it is projected to reach $33.65 billion by 2027.
What are the prominent cybersecurity healthcare trends for 2025? Many hospitals and other healthcare providers will invest more in cybersecurity, including solutions like:
- Access management;
- Secure password management;
- Ransomware protection;
- Secure system integration;
- Data encryption, and more.
Data breaches became the biggest threat to cyber security in the medical sector, and the development of data protection software became one of the prominent cybersecurity healthcare trends in 2025.
Ransomware attacks are among the three major threats to cybersecurity today. Despite being very common, ransomware is extremely dangerous. In 2020, a patient died due to the circumstances created by such an online attack. This tragic incident happened in Germany where ransomware caused locking out of all hospital systems.
As a result, the doctors were unable to accept a new patient to provide urgent care. The patient was taken to a neighboring hospital but it appeared to be too late and she died. This incident shows that ransomware attacks can steal not just data but human lives and we should take cyber threats with all seriousness.
Cybersecurity Trends in Financial Services: Zero Trust, AI, and more
Financial organizations face a lot of threats, such as unauthorized access, customer-sensitive data theft, cryptocurrency-related crimes, and much more. A new trend in cybersecurity for 2025 will be creating new ways to protect financial data and enable safer transactions.
There are some measures you can take to protect your systems and networks in the financial industry:
- Multi-factor authentication;
- “Zero trust” strategy;
- Artificial Intelligence (AI) algorithms;
- Anti-fraud systems based on machine learning;
- Access management, and more.
What is a “zero trust” strategy? It means that your systems must identify and authenticate all users without exceptions. Constant validation includes various methods, including multi-factor authentication that can effectively prevent unauthorized access.
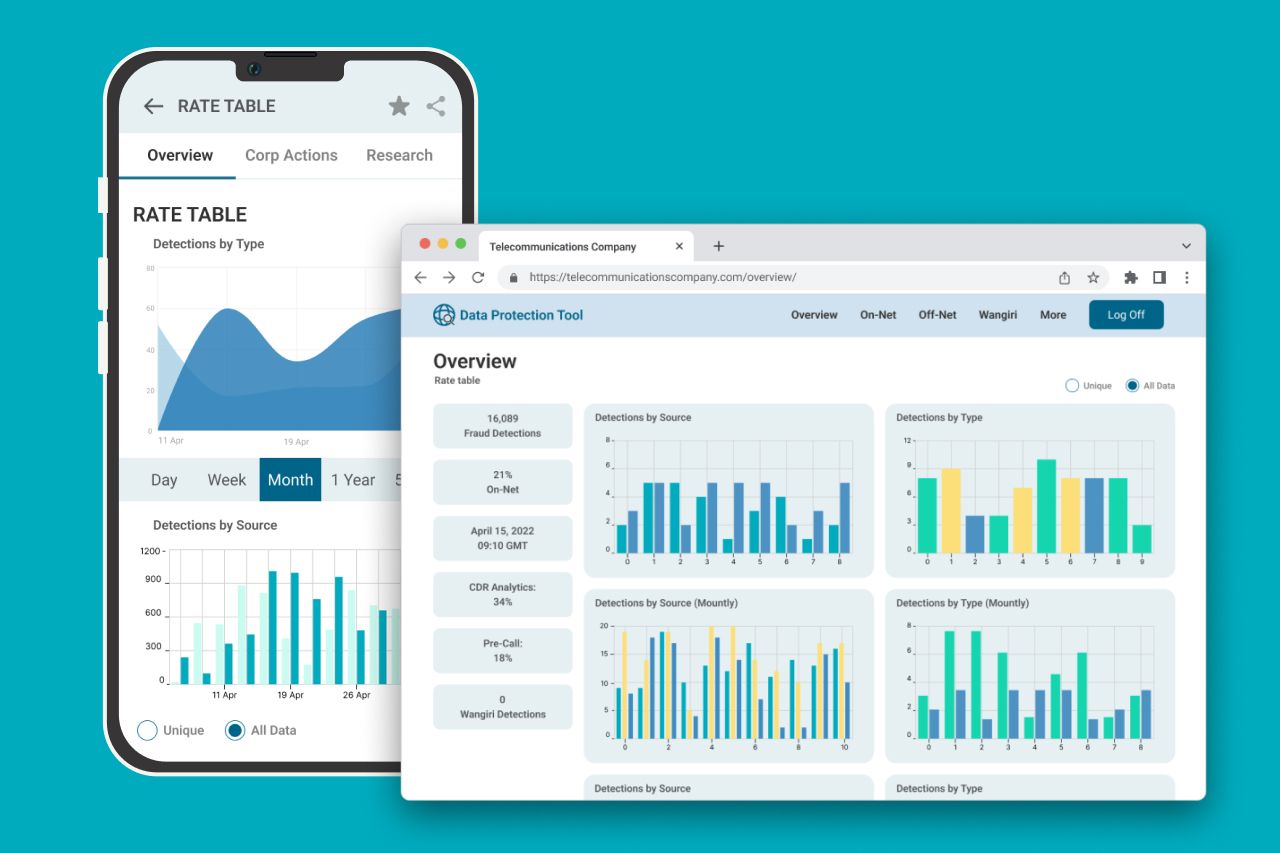
AI algorithms play an increasing role in digital safety, which makes them an integral part of the modern cybersecurity industry and its latest trends. Larger companies can use AI to process huge amounts of client data while mid-sized businesses may work efficiently even if they don’t have enough online security professionals.
This is how Artificial intelligence (AI) allows us to prevent cyberattack attempts:
- Automated security system development;
- Promptly analyzing large amounts of data;
- Automated scanning and threat detection in real-time;
- Scanning for data breaches to notify you instantly;
- New attack prediction;
- Natural language processing;
- Face detection, and more.
On the other hand, cybercriminals are also learning to take advantage of Artificial intelligence, using clever techniques to steal or change data and make their attacks automated. This is why cybersecurity professionals and hackers are constantly racing to invent the newest ways of using AI to maximize efficiency and defeat the other side.
According to the IBM report on cybersecurity spending trends, companies that use Artificial Intelligence to prevent data breaches can save 55.3% of their average online security budget. We expect both AI and Machine Learning to grow in capability and popularity in 2025 to be among the most promising cybersecurity industry trends.
Machine Learning
Machine Learning (ML) is not a new trend in cybersecurity technology – it has been effectively used for years, creating significant opportunities for threat detection. Cyberattacks happen regularly, and a quick response can save a large amount of critical information, business reputation, and lots of money.
Even though cyber threats are continuously evolving, ML allows security specialists to use their efforts more effectively. It provides the following capabilities:
- Creating algorithms to process large data sets;
- Effectively and quickly assess security risks;
- Develop patterns to analyze the habits and techniques of cyber criminals;
- Help prevent similar attacks;
- Make processes simpler for security teams and less expensive for businesses.
Threat detection and fraud detection tools based on programming languages like Python and technologies like AI and Machine Learning. They will be trending cybersecurity solutions to protect from attacks in 2025.
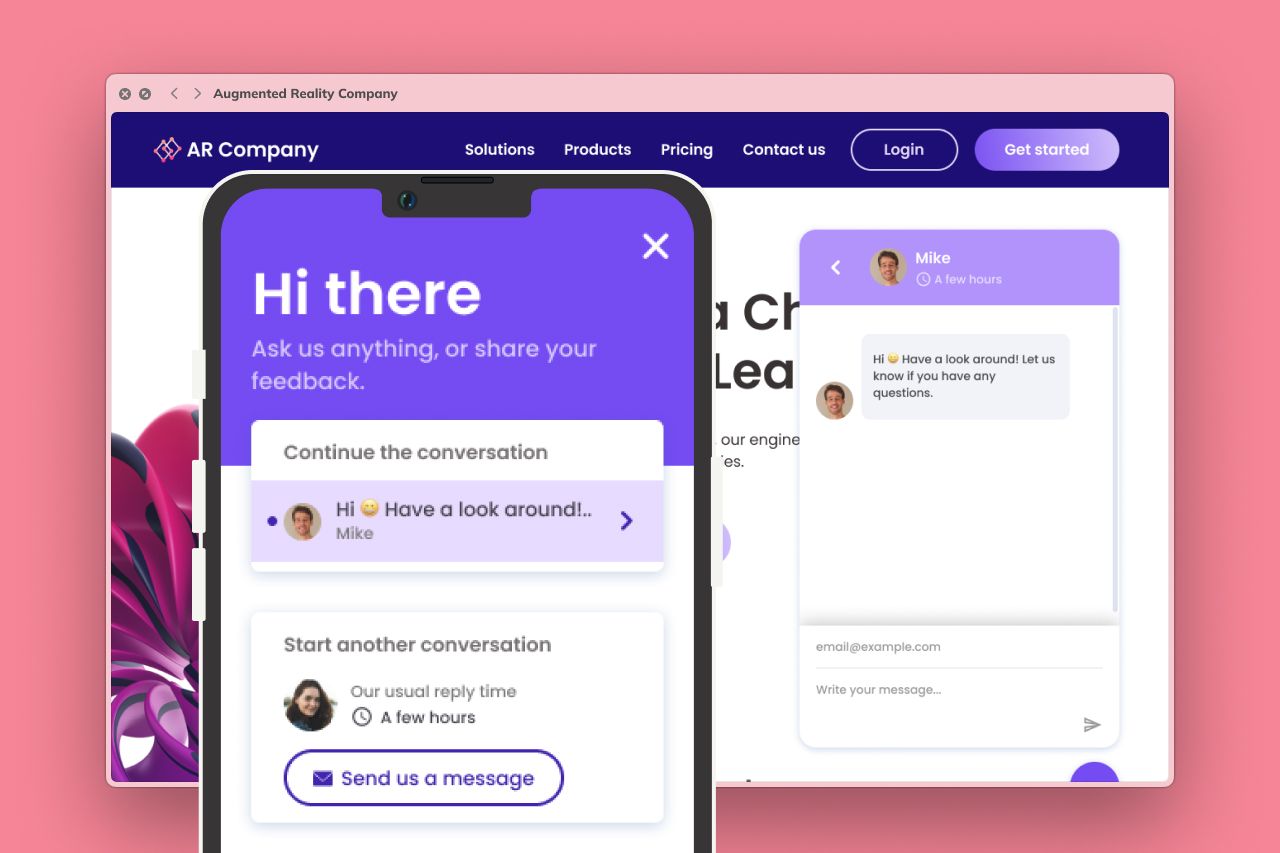
We develop ML elements for various kinds of applications to enable various safety and privacy functions, such as:
- Transaction analysis;
- Fraud detection;
- Access control;
- Virtual assistants;
- Safe password management;
- Digital protection recommendations;
- Risk assessment;
- Threat prediction, and more.
Our specialists also build data analysis software that will be among the prominent trends in cybersecurity shortly. We use programming languages like Python that are ideal for the analysis of huge data sets to identify any suspicious activity. It allows businesses to prevent unauthorized access and protect valuable information by answering questions about errors, vulnerabilities, and risks.
Cybersecurity Insurance Trends: Increase in Automotive Hacking
The clients of any insurance company want to know that their claim will be swiftly and correctly processed while sensitive data like personal and payment information will not fall into the wrong hands. This is why insurance industry businesses closely watch all cybersecurity updates and use threat monitoring systems to prevent data breaches.
There are different types of insurance covering health and life, as well as homes, cars, and other types of property. The rise of automated cars means that the protection of modern systems will be among the most important cybersecurity trends in 2025.
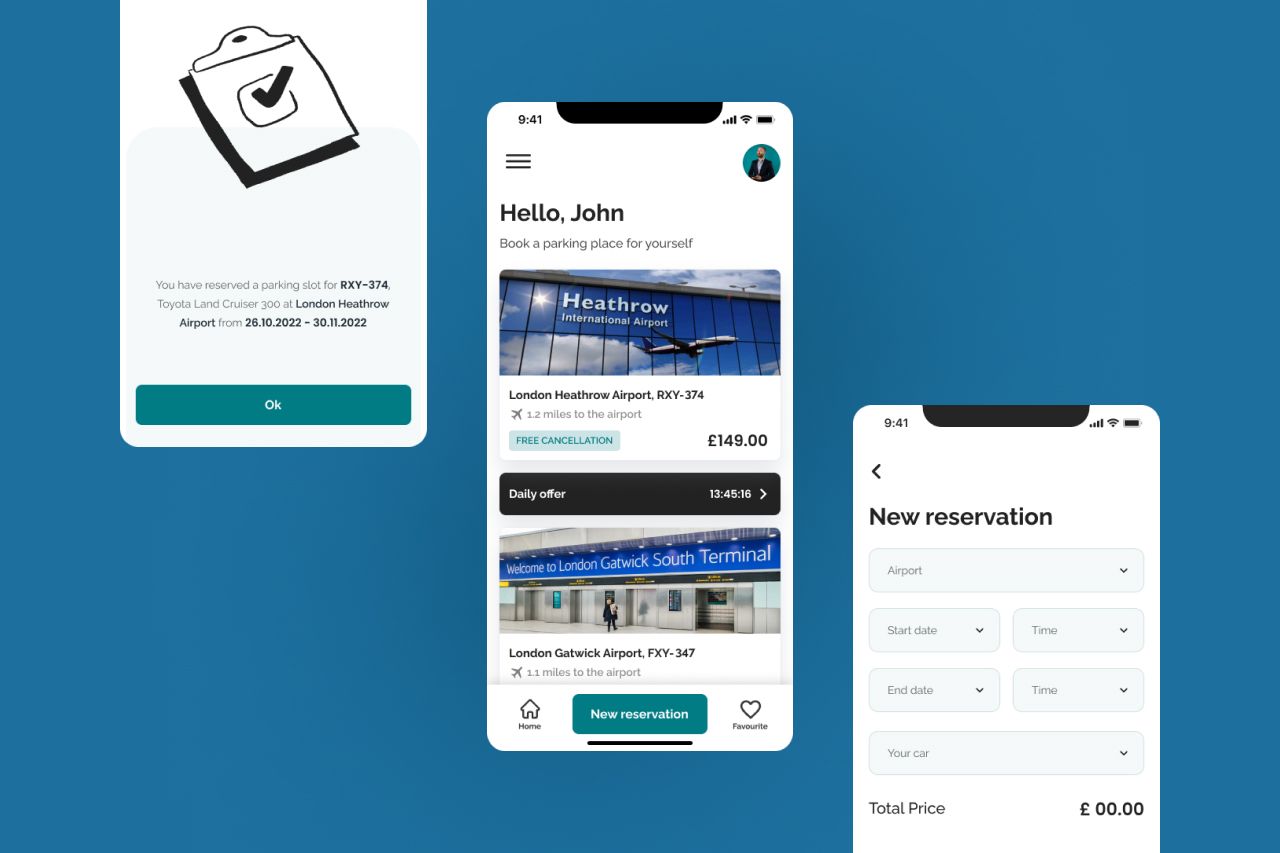
Many vehicles today are equipped with automaton software and IoT solutions that smoothly connect drivers with all the systems, such as control, assistance, locks, airbags, etc. Advanced functions depend on technologies like Wi-Fi and Bluetooth, which means there can be vulnerabilities and threats.
Self-driving cars rely on more complex systems that can also be attacked by digital criminals who want to eavesdrop or take complete control of the vehicle.
Future cybersecurity trends in the insurance industry will include analysis and prevention of cybersecurity risks associated with automotive hacking, IoT solutions, and network protection.
Evolution of IoT
The Internet of Things (IoT) is an evolving and growing technology that includes wearables like smartwatches and fitness bracelets, medical equipment, industrial machinery, home monitoring systems, smart appliances, cars, and much more. This advanced technology is likely to stay with us for decades to come: many researchers estimated that the number of IoT-connected devices will reach 43 billion by 2025 and 64 billion by 2026.
However, there are lots of potential cyber threats related to the use of IoT devices: the more they connect and exchange information, the more opportunities cyber attackers have to catch or change this information or hijack the device.
When it comes to IoT technology, the most common cybersecurity risks include DoS attacks and gaining control of a device. Although IoT units don’t store sensitive data inside themselves, hackers still use them as gateways to other systems and networks.
This is why protecting IoT connections from unauthorized access is extremely important. The challenge is, that such devices usually don’t have capabilities to store and process larger amounts of data, which makes it hard to install antivirus software and threat monitoring applications. Software solutions that enable data protection for IoT-connected devices will be among the new things and developments in cybersecurity in 2025.
Cybersecurity Trends in Higher Education: Ransomware and Other Threats
Colleges and universities face targeted attacks that may include:
- Ransomware attacks;
- SQL injections;
- Phishing attacks;
- Data breaches;
- User carelessness;
- Legacy technology, and more.
Ransomware and phishing are the threats that have existed for decades, but they are constantly changing and evolving as hackers adapt to all cybersecurity technology changes.
Another important factor is remote work and study which became widespread in the pandemic times, creating new targets for online criminals. The growing cybersecurity industry trends in higher education will include developing better protective solutions such as IAM automation and others.
Increase in Cloud Apps: Potential Vulnerabilities
Cloud computing is highly popular as more and more businesses move to the cloud searching for ways to improve their processes. Companies need to establish, monitor, and update their security protocols to prevent all kinds of cybersecurity risks, especially the ones related to remote working with cloud software.
Since data breaches cost around $3.86 million on average, it is important to provide cloud security and network security as well as be prepared for other challenges.
These are typical cloud threats that organizations usually face:
- Network vulnerability that can be a potential entry point for hackers;
- Migration problems;
- Compliance with different security regulations;
- Adequate expertise of IT specialists to manage cloud development and migration, meeting current demands and challenges.
Cloud app development plays a great role in building automation systems for various business industries, making cloud security one of the promising trends of cybersecurity in 2025.
Cloud services are beneficial for many types of businesses, because they provide scalability, process optimization, budget efficiency, and more.
Solutions from Google or Microsoft provide full cybersecurity, but cloud applications are still a primary target for attacks. Misconfiguration of complex settings may cause lots of threats like malware or phishing attacks and issues like data breaches, user profile hijacking, unauthorized access, etc.
An increase in the development and use of cloud applications will continue creating threats to cloud security because more users also mean more insider threats. Many of these issues happen accidentally while some others may be intentional.
Regardless of the cause of insider threats, it is important to protect cloud services from common vulnerabilities:
- Device misuse (remote working is a usual reason why it happens)
- A weak password;
- An unprotected network;
- Unsupervised access (often happens if a company doesn’t use an access management system and role-based access).
The protection of cloud-based infrastructure is an important challenge that will be still trending in cybersecurity in 2025.
Data Protection and Compliance
In 2025 and the years to come, there will be more governmental pressures regarding privacy, sensitive data, and cybersecurity. Gartner predicts that by 2025, 65% of people around the globe will have their personal information protected by laws and regulations.
There are lots of laws and requirements related to digital protection, both in the US and the EU:
- New cybersecurity laws in the major US regions;
- Reporting regulations for important organizations;
- User awareness and reporting requirements from the SEC;
- GDPR compliance.
Some profound laws on data privacy are coming into force in the USA, where many states have already discussed new cybersecurity bills.
According to new requirements in the States, organizations with critically important infrastructure must report ransomware attacks and other online safety incidents from March 2022.
There are also new requirements from the SEC regarding measures and practices of digital protection that all board members should be aware of and report periodically.
GDPR, or General Data Protection Regulation, covers all data protection issues that a consumer from any country of the European Union may ever face. All companies that sell to EU citizens must use the latest cybersecurity developments to protect personal information and other sensitive data, regardless of a customer’s current location.
We are sure that enabling data privacy with the help of cutting-edge technologies will be among the top 13 cybersecurity trends in the healthcare sector, banking, insurance, education, and other industries in 2025.
Mobile Cybersecurity
Mobile-first approach is a promising trend in current web development, because many people spend more than 60% of their daily online time using mobile devices. This also makes smartphones and tablets a new target for cybercriminals.
Remote working makes it habitual for employees to switch between various devices, use collaboration tools, or connect to public Wi-Fi networks. All these actions may possess cybersecurity risks. This is why mobile device protection will become one of the growing trends in cybersecurity in 2025.
According to mobile cybersecurity statistics, Trojans and ransomware attacks are the most common threats that users face when they open banking apps and other software that deals with personal and financial data that must never be disclosed to third parties.
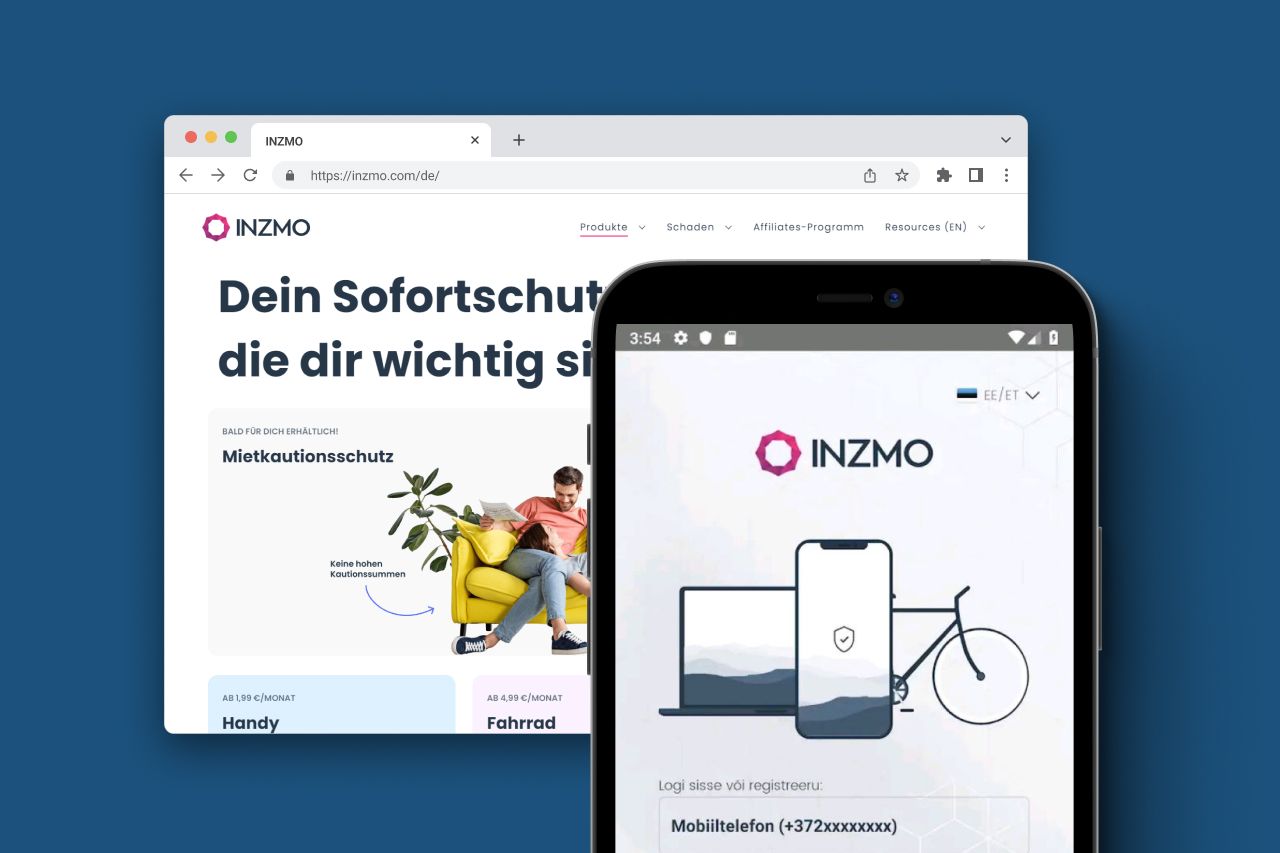
These are typical threats to mobile data protection:
- Spyware attacking encrypted messages;
- Attacks focused on Android devices to find weak spots in security;
- Malware attacks to steal data or spam via SMS;
- DDoS attacks, etc.
5G technology is currently rolling out, which also means creating potential security risks and vulnerabilities. IT security specialists will monitor, measure, predict, and prevent those threats with the help of modern technology.
Mobile cybersecurity is about adding more and more protective layers to cover all possible spots that cybercriminals can use. The elements of mobile safeguarding may include:
- Back-end security;
- Cloud security;
- Network security;
- IoT devices security.
IT security professionals combine software and hardware solutions to protect sensitive data on mobile devices.
Improvements of Multi-Factor Authentication
MFA has been an effective safety solution for years. However, cyber attackers adopted ‘man-in-the-middle’ attacks and other ways of bypassing two-factor authentication procedures enabled with phone calls or SMS. The current security standard is using special keys or app-based authentication methods.
Vulnerabilities of multi-factor authentication create a threat to businesses like online banking, insurance, eCommerce, and more. In 2025, we will see more companies turning towards app-based MFA instead of SMS.
Social Engineering and Targeted Attacks
Financial organizations, healthcare and insurance providers, and large corporations often face targeted attacks aimed at stealing user data or getting access to corporate tools.
Social engineering includes phishing attacks that became widespread during the pandemic with the work-from-home trend. Individual employees become an easier target for hackers who gain information that allows them to infiltrate the company’s network.
Here are some examples of targeted phishing attacks:
- Messaging apps – attackers contact employees on WhatsApp, Slack, WeChat, and other apps and trick people into downloading malicious software;
- Voice phishing – criminals call business representatives and pose as someone else to get valuable data or passwords;
- SIM jacking – a type of targeted attack of mobile operators convincing them to transfer a certain phone number and all connected information to another SIM card.
Social engineering becoming smarter and more technologically advanced is one of the great dangers of cyber crimes. Therefore, developing new ways to safeguard businesses from targeted attacks will be among the cybersecurity trends for 2025.
Wide Range of Cybersecurity Solutions
We have talked about the future of cybersecurity and the latest trends that may shape the industry of digital protection. One more trend for 2025 is a wide range of solutions – web, mobile, cloud, desktop, etc. Companies of different sizes implement various tools to protect sensitive data, analyze risks, optimize outdated software, and more.
Services of custom software development allow businesses to build valuable tools for information protection and risk management.
These are some examples of cybersecurity solutions that we offer to companies around the world:
Password Management Extensions. Secure password managers are built into your favorite browser to ensure safe and convenient access to websites and applications from any computer, laptop, tablet, or smartphone.
Fraud Detection Software. Applications for fraud detection use data analysis techniques, Machine Learning, and an AI-based approach to validate safe operations and detect suspicious ones.
Identity Verification Services. Software for identity verification allows businesses to quickly check if the personal information of their customers is true. Apart from fraud prevention, this helps companies to stay compliant with KYC, AML, and other regulations.
Legacy Software Optimization. Renovation of outdated software is crucial in terms of safety because it allows cybersecurity specialists to strengthen potential weaknesses that may otherwise cause data breaches and open the doors for criminals.
Cloud Development and Cloud Migration. Transfering your databases and software to a safe cloud environment is a new step toward business efficiency and one of the promising cybersecurity industry trends for the near future.
Workflow Automation. Optimizing the flow of information and everyday activities allows a business to monitor the progress in real-time and notice suspicious actions as soon as they occur.
Secure Transactions (API Integration). Payment gateways allow a business to process transactions without risk. We can integrate all kinds of payment solutions according to your requirements.
Do you have any questions about the solutions we provide or some of the cybersecurity technology updates? Don’t hesitate to contact us and discuss your project with experienced cybersecurity professionals.
Need Help With A Project?
Drop us a line, let’s arrange a discussion