How to Build a Chrome Extension for Private Browsing: Common Threats and Security Practices
All you should know about building a private extension for Chrome in 2023.
If you want to develop a Microsoft Edge, Safari, or Chrome extension for private browsing, it makes sense to study what kinds of issues in cybersecurity you may encounter and how to make the browsing experience safe for users.

We will also talk about best practices of secure extension development, regardless of its purpose and the industry it is built for. In addition, we will share our own experience in creating protected solutions for various businesses.
Common Threats to Digital Security: Browser Extensions and Malware Hiding Inside
First and foremost, what are browser extensions? They are special programs that can change browser functionality a little, giving you more opportunities, such as password management, keyword analysis, spelling checks, translations, etc.
You can build extensions with any functionality you need for different purposes like workflow automation, in-browser translation, password management, or SEO optimization. They cater to the needs of various industries, such as eCommerce, Real estate, etc.
These tools work for all popular browsers – you can develop, for example, a Safari extension, a Google Chrome extension, a Microsoft Edge extension, a Firefox extension, and more.
The next important question is – are browser extensions secure? And the answer is not simple, because cybercriminals put much effort into destroying safeguarding systems of extensions to turn them into malware and adware.
Let’s discover some examples of dangers you should know about if you build a Chrome extension for private browsing.
WebSearch
This is a family of adware extensions masking as useful tools such as file converters. They can often deceive you because they start working normally first. However, such an extension installed to your browser will soon perform its true role – track the websites you visit and give you lots of adverts or dangerous links.
How does this adware work? It starts the activity that a secure browser extension would never do. First of all, it uses malicious code to replace your normal browser homepage with a new one that usually contains third-party links, advertisements, etc. Besides, this malicious software will change a default search engine in your browser with some kind of spy program to monitor your browsing history and provide data for cybercriminals.
As for now, users will not run into WebSearch adware when looking for the best browser security extensions in the official Google Chrome Store. They can, however, be accidentally downloaded from third-party websites with free software.
DealPly
This family of malicious add-ons can infiltrate your computer if you download content from not-so-trustworthy websites. This type of adware works quite similarly to the WebSearch family, creating a new homepage and collecting information about the websites you visit. The important difference is that DealPly add-ons are very hard to delete completely, because the malicious code they use installs them again once you open a web browser.
It is vital for you to know about such threats if you are planning to build your own Safari or Chrome private browsing extension.
AddScript
Malware from the AddScript family infects users’ devices with unwanted cookies or malicious code that changes the way these devices work. For example, a very common case is pretending to be tools for downloading media files from social networking sites. Once a user installs such an extension, browser software starts playing videos to increase the number of views, and the user may not notice it because everything happens in the background mode.
You will not normally find such dangerous extensions in Chrome Web Store, because technical teams find and delete them. However, dangerous tools are often offered on third-party websites. It is important to keep in mind what kind of dangerous scenarios attackers may use if you are going to develop your own tool for secure browsing.
FB Stealer
This is a family of adware extensions designed by cyber criminals to steal Facebook session cookies and later get access to profiles of as many users as possible to send messages from their names and commit all kinds of frauds. The main source from which people can get FB Stealer is using software installers that have been hacked.
How to Enable User Protection Working with Browser Extensions
The main danger of malicious software is that it pretends to be a regular tool to let the users’ guide down.
If you want to build a highly secure browser extension and protect it from cyber attacks, we recommend partnering with experienced and reliable companies that specialize in browser extension development.
If your organization uses a variety of extensions and add-on for work, make sure that you and your employees understand the basics of using such software for a secure browsing experience.
- Use only tools from official sources like Chrome Web Store, App Store, and others. Unfortunately, it is not a 100% guarantee that you will never come across a malicious extension there, but these platforms put a lot of effort into safety measures and remove dangerous software once they detect it. Web stores are excellent sources where you can find the best browser extensions for security and privacy.
- Do not install more extensions than you can easily manage. This way, you will be able to check them regularly and see if something looks like a red flag.
- Use trustworthy solutions for online security.
- Choose experienced development teams to build software like a password keeper, security browser extension, access management tool, etc.
How to Enable Privacy for Browsing Experience
There are different ways to enable secure and private web browsing. Some extensions are designed specifically for this purpose – for example, Ghostery, ExpressVPN, Click and Clean, Team Password, and Malwarebytes Browser Guard are among the best Chrome extensions for privacy and security. The role of Chrome extensions in private browsing is extremely important.
Sometimes businesses create extensions to be used solely within employees or clients. It is a great way to protect sensitive information from third parties, just like making a web portal for customers that provides limited access to your company’s resources. There are many browsers for a private browsing extension: Chrome, Safari, Microsoft Edge, etc.
Many people use a private browsing mode to protect their browsing history and other information online. Google Chrome, which is one of the most secure web browsers, is highly popular, but has one disadvantage – it disables any extensions when you are in private browsing mode. To use extensions in a private mode, browser settings should be changed a little.
Chrome’s incognito mode works with extensions when a user follows these steps:
- Clicking on the three dot icon in the upper right corner – Selecting ‘More Tools’ and then ‘Extensions’.
- Finding an extension you would like to enable in Incognito mode and clicking on ‘Details’.
- Scrolling down to ‘Allow in Incognito’ to enable an extension permission. It’s done! Now you can use the chosen extension every time you open a new incognito window.
You may want to provide users with this information if you are building a new Chrome extension for private browsing. It is also important to note that you can create tools for other browsers as well. Some of them (for example, Safari) don’t restrict users from using extensions in Incognito mode.
How to Build Tools for Secure and Private Browsing: Chrome Extension Software and Others
Cybersecurity is highly important in today’s world, because all businesses work with digital assets and use the Internet to spread data. Many companies apply security best practices such as:
- IAM or Identity-Access Management automation;
- reliable password keepers;
- role-based access features;
- secure invoice workflow processing tools, etc.
If you are wondering how you can make Chrome extensions secure or protect other browser tools from threats, we will tell you about best practices.
Tip#1: Be careful sharing objects with in-page JavaScript
Cyber criminals can use malicious code and add certain modifications to JavaScript object functions so that an extension does whatever the intruders want.
Tip#2: Do not use JavaScript for Google Analytics
When it comes to Chrome extensions, private browsing is a must in any case, and especially when you add third-party services like Google Analytics. However, we would like to warn you against using the JavaScript code.
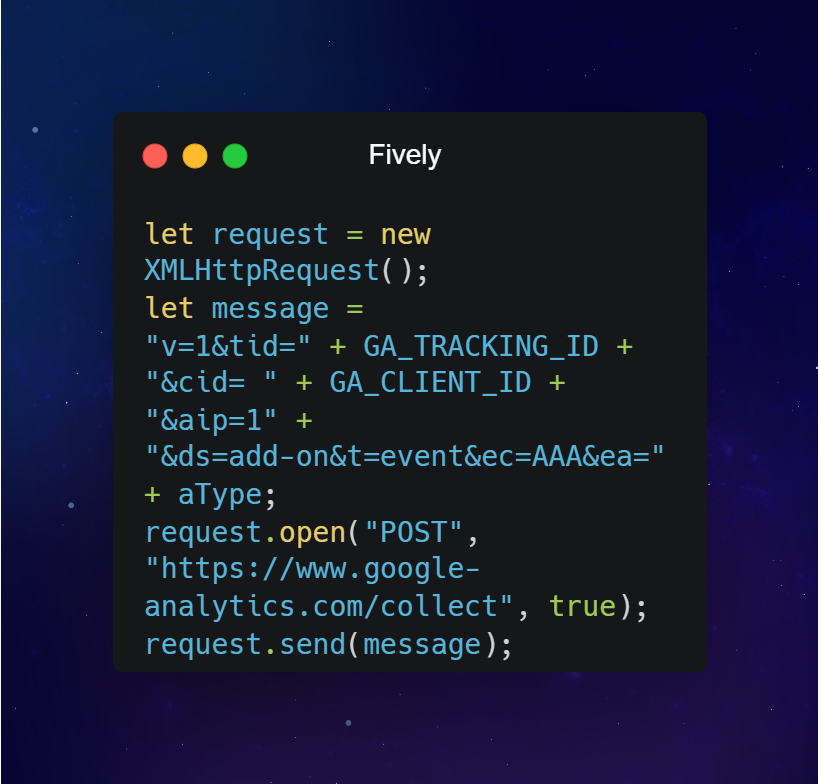
Google Analytics REST API in an XHR call is a much better solution. Here is how you can do it:
Tip#3: Never apply remote scripts
If you research how the best browser extensions for security work you will find out that they may use third-party services but do not inject any scripts from remote sources and rather have copies of these scripts in their codebases.
The main danger of a remote script is the fact that you don’t control it. Even if nothing bad happens, the fact that a third party changes some code without your and your users’ consent will certainly compromise the security.
Tip#4: Apply safety best practices when using remote content
Such practices usually include:
- Inserting strings with safe methods for native DOM manipulation, such as Node.textContent, Element.setAtttribute(), and document.createElement() that are recommended by Firefox and Chrome private browsing extension developers;
- Applying text(), attr(), and other jQuery functions;
- Using DOMPurify to sanitize HTML content;
- Using template engine commands.
Tip#5: Create the UI with built-in features
There are plenty of built-in components for the best browser security extensions – in Firefox, Chrome, Safari and others. These components include pageAction, browserAction, bundled pages, etc. Do not add toolbars, buttons and other UI components directly to web pages. This can compromise extension security.
Tip#6: Check your third-party libraries for updates
Make sure that all third-party libraries that you use are up-to-date and therefore secure. When your libraries have updates, you should also update your extension – browser software may be blocked in stores if it uses outdated components.
Tip#7: Leave third-party libraries untouched
When you use third-party libraries and try to modify some code in them, it may be seen as malicious code injection. If you don’t want your extension to be disabled in stores, never do anything to third-party code.
Tip#8: Never inject any content directly
This applies to links, images and other types of content, because it can be traced by hackers and therefore presents a threat to cybersecurity and private browsing – Chrome extension software should not let any information fall into the criminal hands.
Tip#9: Be careful using window.eval()
The use of window.eval() is risky, because cyber criminals can benefit from it and run their own code on your web pages. The best browser security extensions don’t use eval() and select safer methods instead – Function(), for example.
Tip#10: Use a standard Content Security Policy
Safari, Google Chrome, Microsoft Edge, Firefox – each web browser utilizes similar security policies. It allows your extension to avoid potentially dangerous sources to load <script> and <object> from, as well as unsafe practices and other threats. For the sake of security, we don’t recommend making any changes to a standard Content Security Policy.
How Fively Can Help You Build a Secure Browser Extension
Web development experts at Fively create different types of extensions and add-ons for Google Chrome, Safari, and Microsoft Edge as the most popular browsers nowadays.
With us, you can develop all kinds of programs for private and safe web experiences: security browser tools for business automation, access management software, a reliable password keeper, security browser extension tools for eCommerce, etc.
Our in-house team includes 100+ specialists in web development, QA, design, business analysis, and project management. We provide Safari, Microsoft Edge, and Google Chrome extension development services for various business industries, for example:
- FinTech;
- Social media;
- eCommerce;
- Marketing and Advertising;
- Media and Entertainment;
- Real Estate;
- Cyber Security.
Our approach to secure browser extension development is based on data analytics, customer research, modern designing and engineering solutions and cutting-edge technologies. We partner with various enterprises and startups worldwide.
Would you like to develop a Chrome extension for private browsing and give your customers or employees more possibilities while keeping web experience secure? Let’s talk about your project. Business analysts at Fively will help select impactful features and the right development approach in accordance with your business goals.
Need Help With A Project?
Drop us a line, let’s arrange a discussion